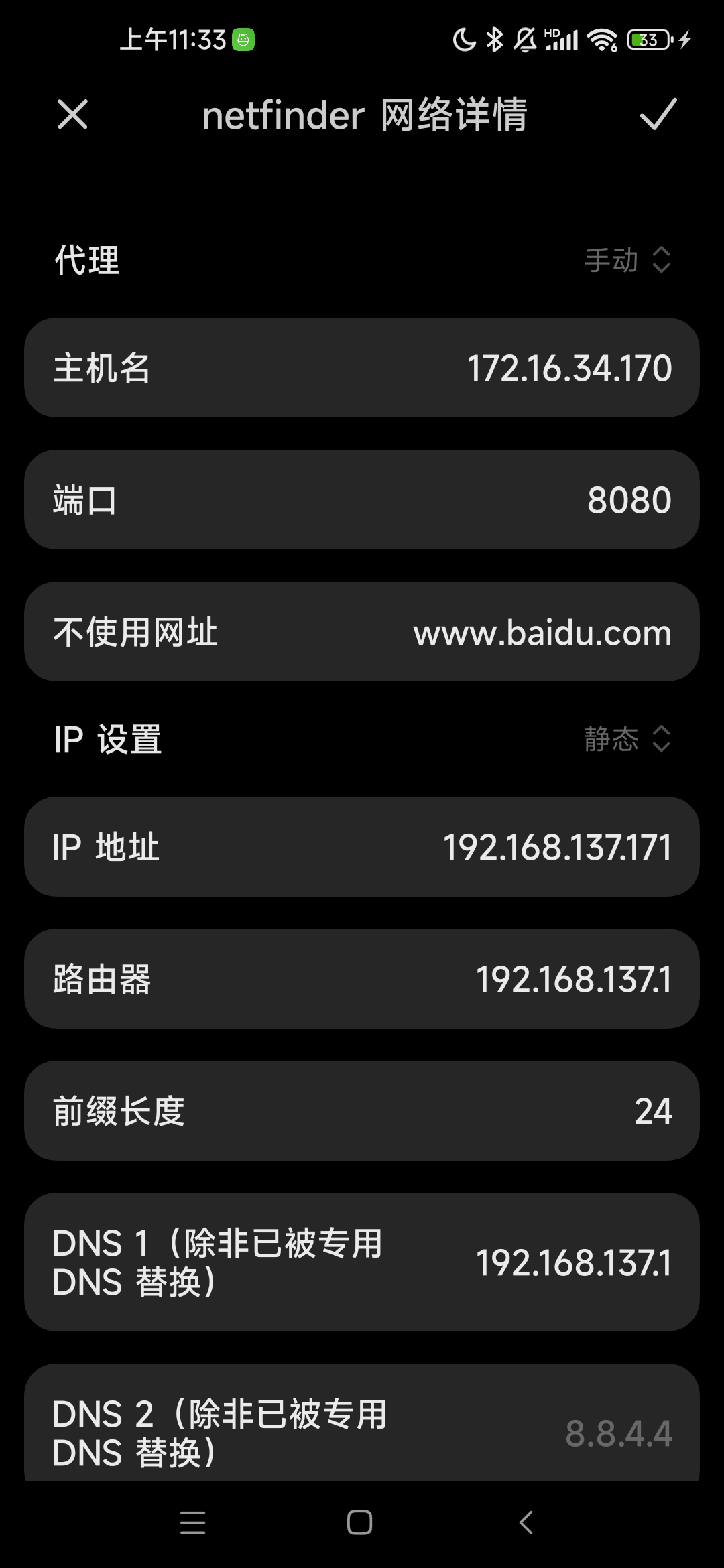
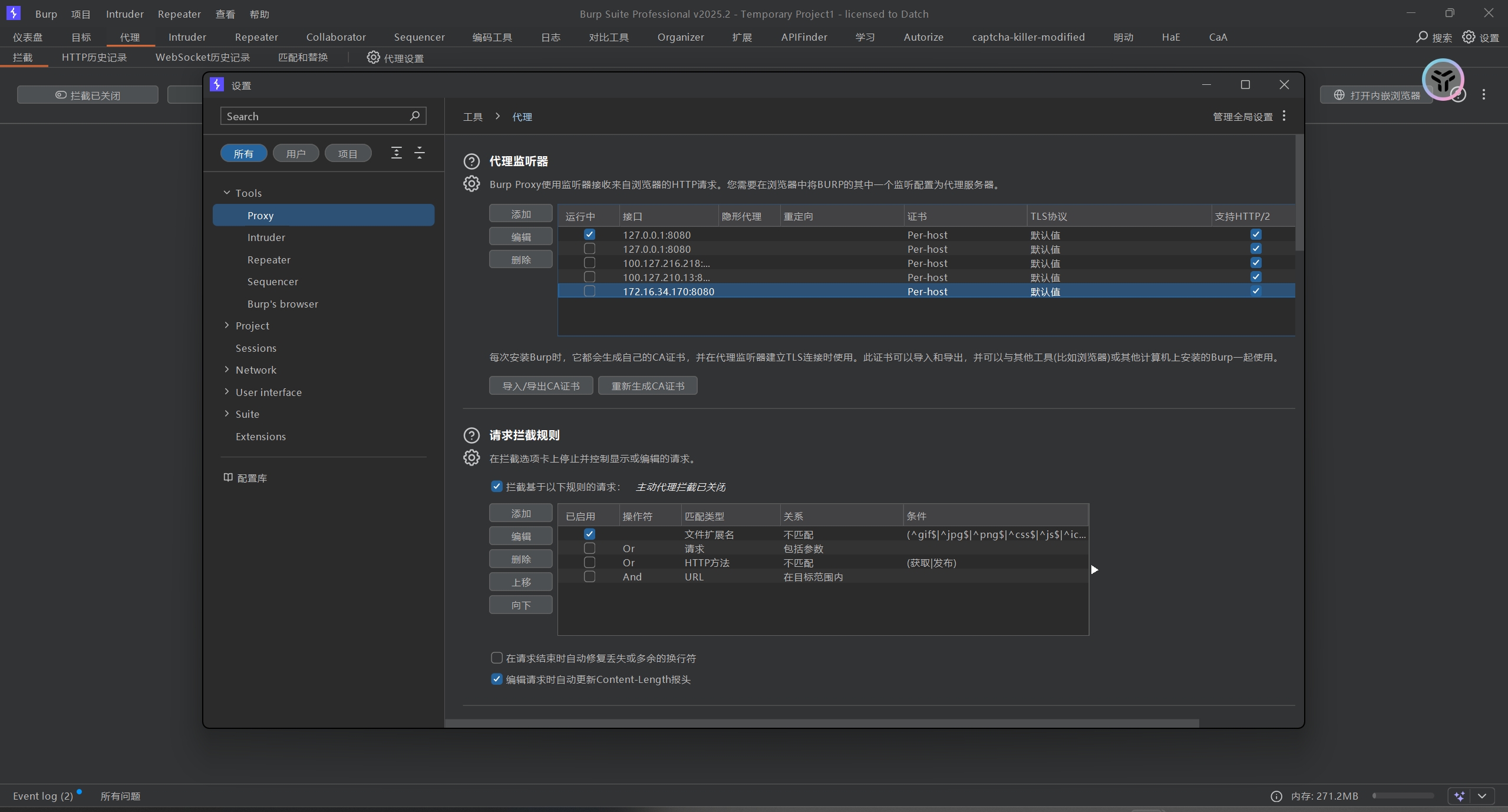
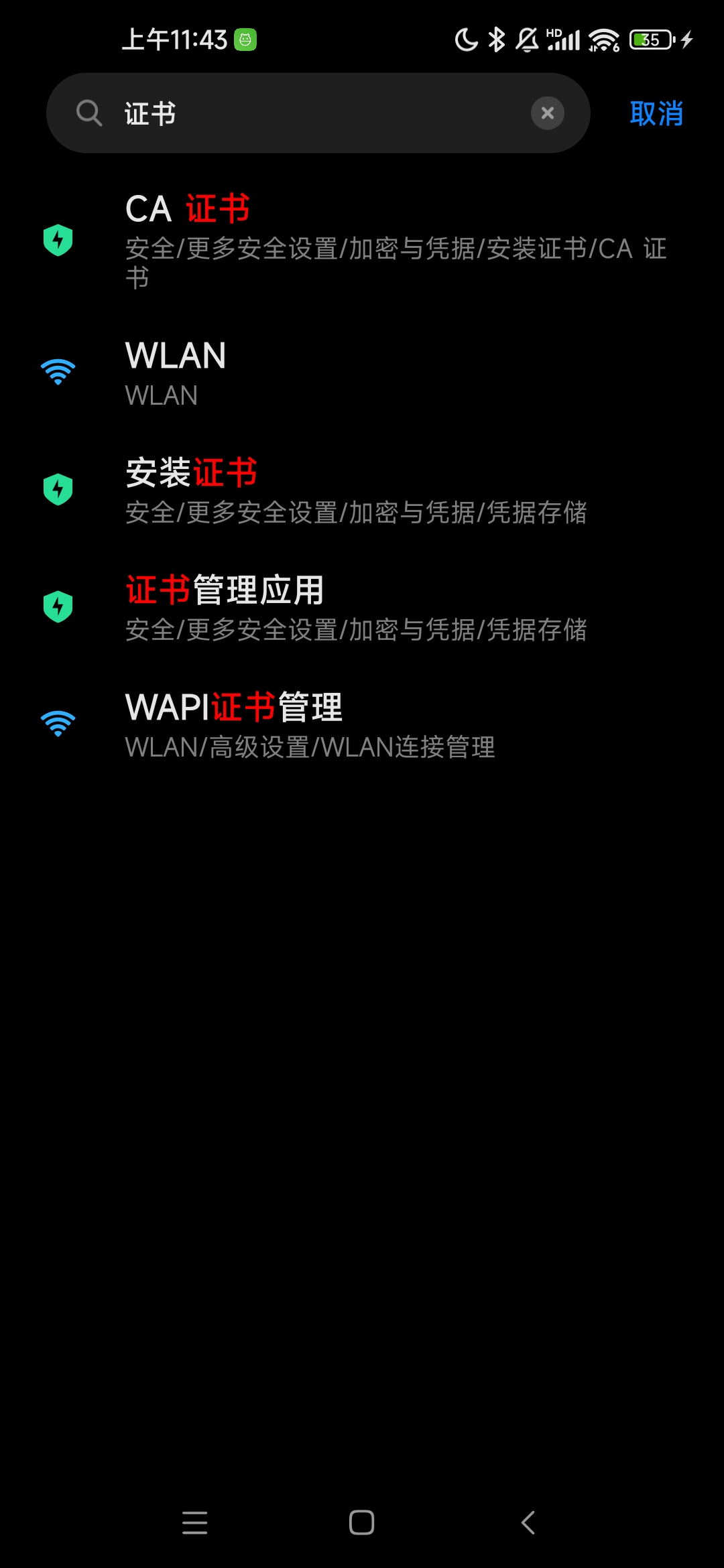
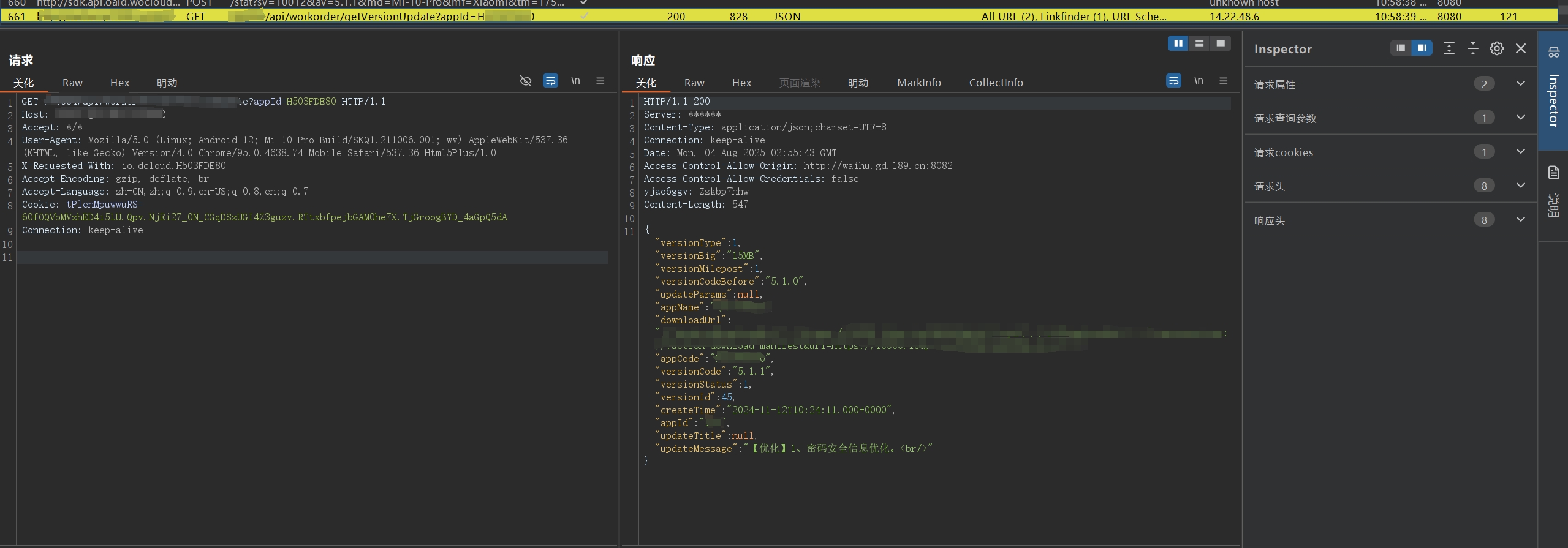
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
|
function hook_dlopen(so_name) {
Interceptor.attach(Module.findExportByName(null, "android_dlopen_ext"), {
onEnter: function (args) {
var pathptr = args[0];
if (pathptr !== undefined && pathptr != null) {
var path = ptr(pathptr).readCString();
if (path.indexOf(so_name) !== -1) {
this.match = true;
}
}
},
onLeave: function (retval) {
if (this.match) {
console.log(so_name, "加载成功");
var base = Module.findBaseAddress("libDexHelper.so");
patch_func_nop(base.add(322008));
patch_func_nop(base.add(308756));
patch_func_nop(base.add(350196));
patch_func_nop(base.add(372648));
}
}
});
}
function patch_func_nop(addr) {
Memory.patchCode(addr, 8, function (code) {
code.writeByteArray([0xE0, 0x03, 0x00, 0xAA]);
code.writeByteArray([0xC0, 0x03, 0x5F, 0xD6]);
console.log("patch code at " + addr);
});
}
hook_dlopen("libDexHelper.so");
function hajimi() {
var clone = Module.findExportByName('libc.so', 'clone');
Interceptor.attach(clone, {
onEnter: function (args) {
if (args[3] != 0) {
var addr = args[3].add(96).readPointer();
var so_name = Process.findModuleByAddress(addr).name;
var so_base = Module.getBaseAddress(so_name);
var offset = (addr - so_base);
console.log("===============>", so_name, addr, offset, offset.toString(16));
}
},
onLeave: function (retval) {}
});
}
hajimi();
setImmediate(function() {
console.log("[*] Waiting for Traffic");
console.warn("[*] Please Check Target Hosts section in the code, if u dont see requests");
Java.perform(function() {
var okhttp3 = Java.use('okhttp3.OkHttpClient');
var webViewClient = Java.use('android.webkit.WebViewClient');
var redColor = '\u001b[31m';
var greenColor = '\u001b[32m';
var resetColor = '\u001b[0m';
var targetHosts = [];
var originalNewCall = okhttp3.newCall.overload('okhttp3.Request');
originalNewCall.implementation = function(request) {
console.log(Java.use("android.util.Log").getStackTraceString(Java.use("java.lang.Throwable").$new()));
var requestUrl = request.url().toString();
var urlParts = requestUrl.split("/");
var extractedHost = urlParts[2];
console.log("request url: ", requestUrl)
console.log("request parts: ", urlParts)
console.log("extractedHost: ", extractedHost)
if (targetHosts.includes(extractedHost) || targetHosts.length === 0) {
var requestEndpoint = requestUrl.replace(/^(https?:\/\/[^\/]+)(\/.*)$/, '$2');
var requestHeaders = request.headers();
console.log(redColor + "[API Call]" + resetColor);
console.log(" ");
console.log(greenColor + request.method() + " " + requestEndpoint);
requestHeaders = requestHeaders.newBuilder()
.add("Host", extractedHost)
.build();
var requestHeaderNames = requestHeaders.names();
var requestHeaderNamesArray = requestHeaderNames.toArray();
for (var i = 0; i < requestHeaderNamesArray.length; i++) {
var headerName = requestHeaderNamesArray[i];
var headerValue = requestHeaders.get(headerName);
headerValue = decodeURIComponent(headerValue);
console.log(greenColor + headerName + ": " + headerValue + resetColor);
}
console.log(" ");
console.log(" ");
console.log(greenColor + requestBodyToString(request.body()) + resetColor);
console.log(redColor + "============================" + resetColor);
var newRequest = request.newBuilder().headers(requestHeaders).build();
var response = this.newCall(newRequest).execute();
console.log(redColor + "[API Response]" + " - [" + requestEndpoint + "]" + resetColor);
console.log(" ");
console.log(greenColor + response.code() + " " + response.message() + resetColor);
var responseHeaders = response.headers();
var responseHeaderNames = responseHeaders.names();
var responseHeaderNamesArray = responseHeaderNames.toArray();
for (var i = 0; i < responseHeaderNamesArray.length; i++) {
var responseHeaderName = responseHeaderNamesArray[i];
var responseHeaderValue = responseHeaders.get(responseHeaderName);
console.log(greenColor + responseHeaderName + ": " + responseHeaderValue + resetColor);
}
console.log(" ");
var responseBody = response.body();
if (responseBody !== null) {
if (response.isSuccessful()) {
console.log(greenColor + responseBody.string() + resetColor + resetColor);
} else {
console.log(redColor + "Error: Response not successful" + resetColor);
}
} else {
console.log(greenColor + "Error: Empty response body" + resetColor);
}
console.log(redColor + "============================" + resetColor);
return this.newCall(request);
} else {
return this.newCall(request);
}
};
var shouldOverrideUrlLoading = webViewClient.shouldOverrideUrlLoading.overload('android.webkit.WebView', 'java.lang.String');
shouldOverrideUrlLoading.implementation = function(view, url) {
console.log(redColor + "[WebView URL]: " + url + resetColor);
return shouldOverrideUrlLoading.call(this, view, url);
};
get_data();
});
});
function requestBodyToString(requestBody) {
if (requestBody === null) {
return '';
}
var buffer = Java.use('okio.Buffer').$new();
requestBody.writeTo(buffer);
return buffer.readUtf8();
}
const Color = {
Red: '\x1b[31m',
Green: '\x1b[32m',
Yellow: '\x1b[33m',
Blue: '\x1b[34m',
Reset: '\x1b[0m'
};
function colorLog(msg, opts) {
const c = opts?.c || Color.Reset;
console.log(c + msg + Color.Reset);
}
Java.perform(function() {
colorLog('\n----------DEEPLINK DATA MONITOR (GETDATA ENHANCED)------------', {c: Color.Yellow});
var Intent = Java.use('android.content.Intent');
if (Intent.$init) {
Intent.$init.overload('java.lang.String', 'android.net.Uri').implementation = function(action, uri) {
const retval = this.$init(action, uri);
if (uri) {
colorLog('\n[+] Deeplink 初始化 (构造函数)', {c: Color.Green});
colorLog('------Intent 信息------', {c: Color.Blue});
console.log('[+] Action: ' + action);
console.log('[+] Deeplink Data: ' + uri.toString());
colorLog('-----------------------', {c: Color.Blue});
}
return retval;
};
}
Intent.setData.overload('android.net.Uri').implementation = function(uri) {
const retval = this.setData(uri);
if (uri) {
colorLog('\n[+] Deeplink 数据设置 (setData)', {c: Color.Red});
colorLog('------Intent 信息------', {c: Color.Blue});
console.log('[+] Action: ' + this.getAction());
console.log('[+] Deeplink Data: ' + uri.toString());
console.log('[+] Flags: ' + this.getFlags());
colorLog('-----------------------', {c: Color.Blue});
}
return retval;
};
Intent.setDataAndType.overload('android.net.Uri', 'java.lang.String').implementation = function(uri, type) {
const retval = this.setDataAndType(uri, type);
if (uri) {
colorLog('\n[+] 带类型 Deeplink 数据设置 (setDataAndType)', {c: Color.Yellow});
colorLog('------Intent 信息------', {c: Color.Blue});
console.log('[+] Action: ' + this.getAction());
console.log('[+] Deeplink Data: ' + uri.toString());
console.log('[+] MIME Type: ' + type);
colorLog('-----------------------', {c: Color.Blue});
}
return retval;
};
Intent.getData.implementation = function() {
const uri = this.getData();
if (uri) {
colorLog('\n[!] Deeplink 数据被获取 (getData)', {c: Color.Green});
colorLog('------获取到的 Uri 信息------', {c: Color.Blue});
console.log('[+] Uri 完整路径: ' + uri.toString());
console.log('[+] Scheme: ' + uri.getScheme());
console.log('[+] Host: ' + uri.getHost());
console.log('[+] Path: ' + uri.getPath());
console.log('[+] Query: ' + uri.getQuery());
colorLog('----------------------------', {c: Color.Blue});
}
console.log(Java.use("android.util.Log").getStackTraceString(Java.use("java.lang.Throwable").$new()));
return uri;
};
Intent.getDataString.implementation = function() {
const dataStr = this.getDataString();
if (dataStr) {
colorLog('\n[!] Deeplink 字符串被获取 (getDataString)', {c: Color.Red});
colorLog('------获取到的字符串信息------', {c: Color.Blue});
console.log('[+] Data String: ' + dataStr);
colorLog('------------------------------', {c: Color.Blue});
}
console.log(Java.use("android.util.Log").getStackTraceString(Java.use("java.lang.Throwable").$new()));
return dataStr;
};
});
|